
Simplifying Network Forensic Analysis: Exploring Wireshark PCAP Files with Brim
Wireshark is a powerful network protocol analyzer that allows network administrators and security professionals to monitor and inspect network traffic. It captures packets in real-time or reads from existing capture files, known as PCAP files, for offline analysis. However, as the complexity of network data increases, analyzing PCAP files can become cumbersome. In this blog post, we’ll introduce Brim, a modern and intuitive tool that simplifies the process of viewing and analyzing Wireshark PCAP files, making network analysis more efficient and insightful.
Understanding PCAP Files
A PCAP (Packet Capture) file is a data file that contains captured network packets in a standardized format. Wireshark generates these files when capturing live traffic or when reading from previously recorded sessions. PCAP files store packet information, including source and destination IP addresses, ports, protocols, timestamps, and more. These files are invaluable for diagnosing network issues, detecting anomalies, and investigating security incidents.
Introducing Brim
Brim is a state-of-the-art network analysis tool designed to help users make sense of vast amounts of network data, including Wireshark PCAP files. It provides an elegant and user-friendly interface that simplifies the process of exploring complex network datasets. Brim’s unique approach combines speed, scalability, and advanced search capabilities, making it an excellent choice for both novices and experienced analysts.
Key Features of Brim:
Intuitive Interface: Brim’s interface is designed with the user in mind. The clean and modern layout allows for easy navigation and efficient analysis, eliminating the steep learning curve associated with many network analysis tools.
High Performance: Brim leverages cutting-edge technologies to handle large PCAP files with lightning-fast speed. Analyzing massive datasets is no longer a time-consuming task.
Timeline View: Brim offers a timeline view that allows users to visualize network events over time. This feature helps in identifying patterns, understanding traffic trends, and spotting irregularities.
Dynamic Filtering: Brim’s filtering capabilities are second to none. Users can quickly narrow down their searches using various criteria, such as IP addresses, ports, protocols, and timestamps.
Advanced Query Language: Brim incorporates an expressive query language that enables users to create complex searches and analyze data with precision.
Later, we will run Wireshark to collect network traffic in a Sandbox (Windows 10) Lab machine with the goal of analyzing any network connections made from a known Agent Tesla sample.
Agent Tesla: The RAT
Agent Tesla” is known as a type of Remote Access Trojan (RAT). A RAT is a malicious software program used by cybercriminals to gain unauthorized access and control over a victim’s computer remotely. Once installed on a target system, a RAT allows the attacker to perform various malicious activities, such as stealing sensitive information, logging keystrokes, capturing screenshots, accessing files, and even controlling the victim’s computer. The RAT’s primary purpose is to gather and exfiltrate valuable information from infected systems, which can then be used for various malicious purposes, such as identity theft, financial fraud, or selling the stolen data on the dark web.
How This Agent Tesla malware is delivered
Agent Tesla is typically delivered to the victim through various methods, including phishing emails, malspam, and exploit kits. The exact method of delivery may vary depending on the attackers’ goals.
In this instance, one of my customers received this malware through malspam; which contained a malicious .exe file (Agent Tesla) within a tar.gz archive named TT remittance against outstanding invoice.tar.gz. The malicious executable file (TT remittance against outstanding invoice.exe), that once clicked, it runs and executes.
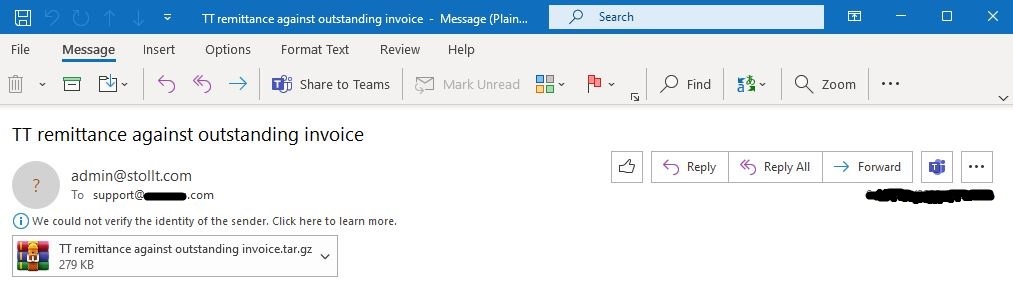 Figure 1: Malspam which contained a malicious .exe file (Agent Tesla) within a tar.gz archive named TT remittance against outstanding invoice.tar.gz
Figure 1: Malspam which contained a malicious .exe file (Agent Tesla) within a tar.gz archive named TT remittance against outstanding invoice.tar.gz
Agent Tesla – Data Exfiltration over SMTP
I reviewed the post infection traffic from this malware using Wireshark and Brim. The review of the Wireshark capture reveals a DNS request for smtp.marintravellft.com. This was the start data exfiltration over SMTP.
![]() Figure 2: Wireshark capture of C2 traffic show a DNS request to smtp.marintravellft.com.
Figure 2: Wireshark capture of C2 traffic show a DNS request to smtp.marintravellft.com.
Next, I seen successful authentication to a compromised email address (schayer@marintravellft.com). The body of the email shows that customer data is being exfiltrated, which includes the hostname, ip address, and username of the infected host machine.
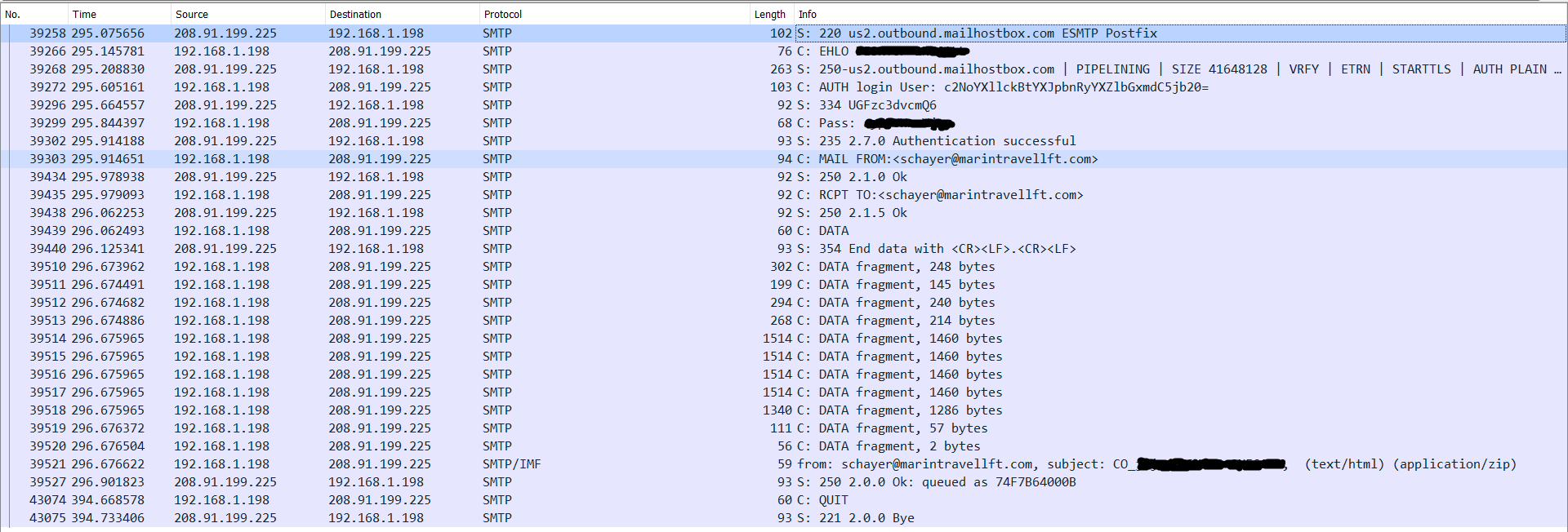 Figure 3: Wireshark capture of C2 Traffic showing a successful connection over SMTP.
Figure 3: Wireshark capture of C2 Traffic showing a successful connection over SMTP.
.
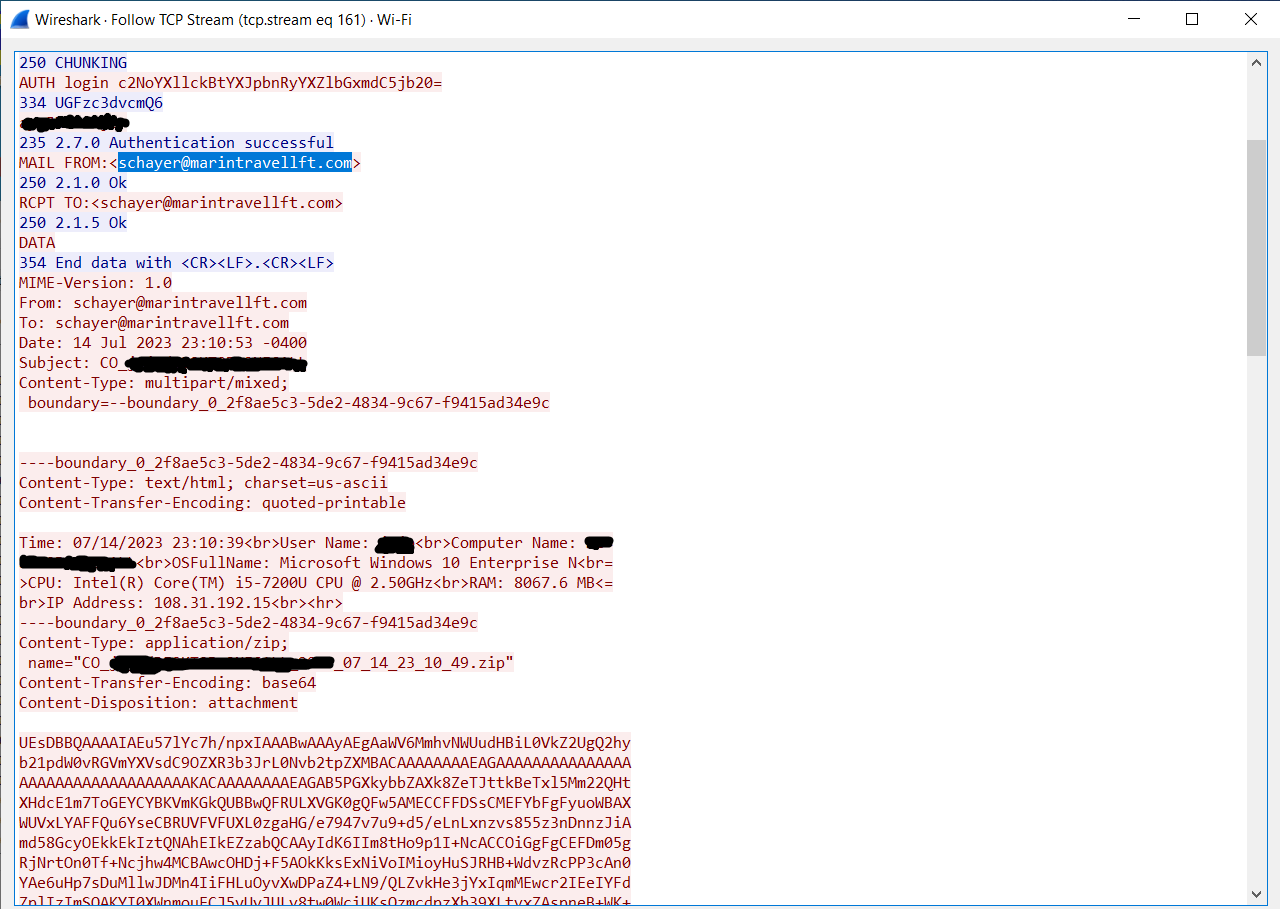 Figure 4: Wireshark capture of C2 traffic showing customer data being sent to a compromised email address (schayer@marintravellft.com).
Figure 4: Wireshark capture of C2 traffic showing customer data being sent to a compromised email address (schayer@marintravellft.com).
Agent Tesla – Exfiltration detected by Brim’s Suricata
Lastly, I loaded the Wireshark PCAP file into Brim. Brim’s Suricata signatures were able to detect and alert on the C2 connection to IP 208.91.199.224:587, which is the data exfiltration over SMTP.
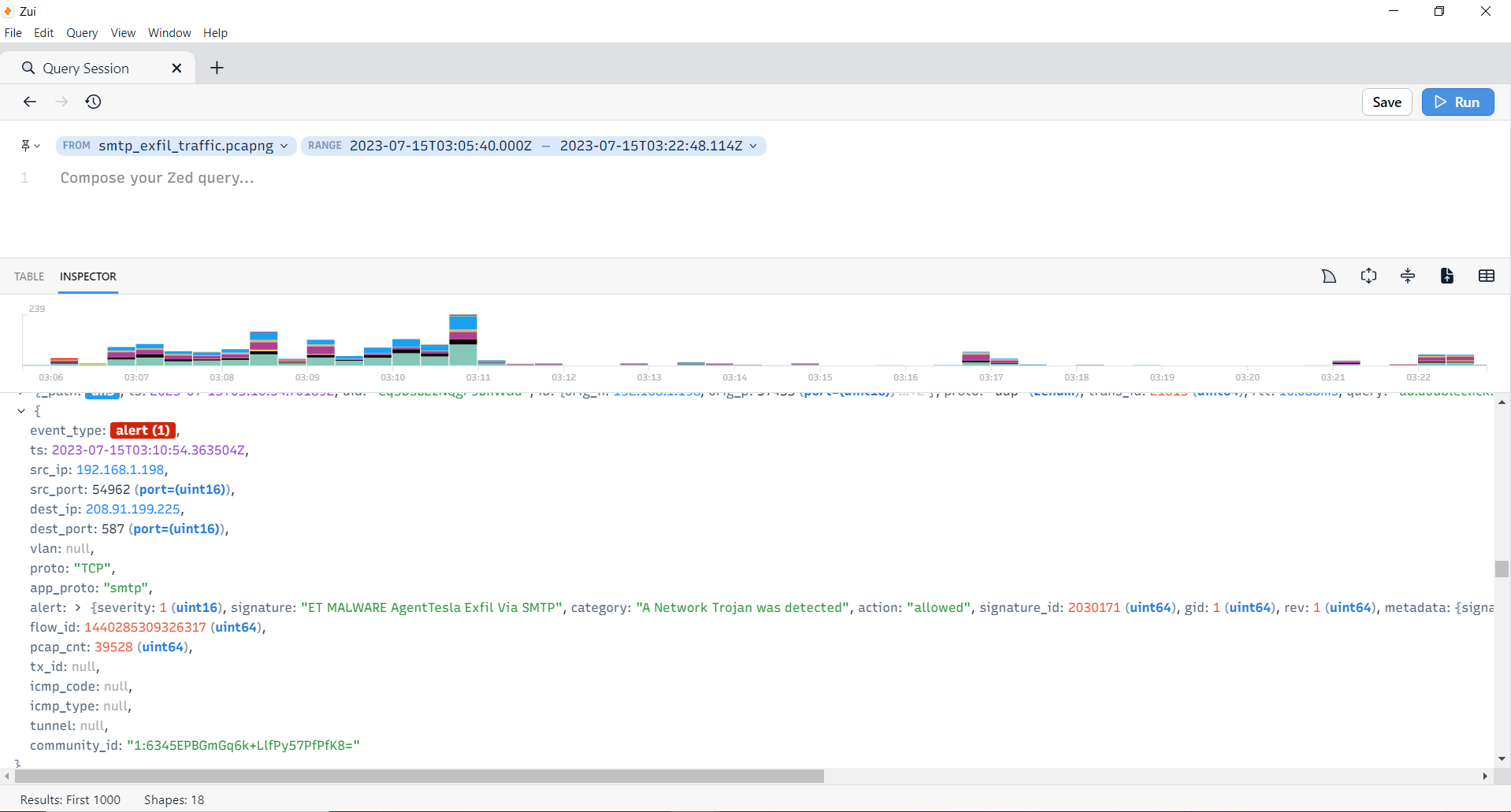 Figure 5: Brim’s Suricata engine detects the data exfiltration over SMTP.
Figure 5: Brim’s Suricata engine detects the data exfiltration over SMTP.
That ends this blog, where we used Wireshark and Brim to collect and analyze network traffic from stage 1 of this Agent Tesla infection.
IOCs:
TT remittance against outstanding invoice.tar.gz (MD5: 3f2deec2e3e8871ec4d0e2c68fc81804)
TT remittance against outstanding invoice.exe (MD5: e636239783988acde754d1555dcd1986)
C2 IOCs:
smtp.marintravellft.com
us2.smtp.mailhostbox.com
208.91.199.224:587
