Formbook: A Infostealer
Formbook is a type of malware that is primarily used for stealing sensitive information from infected computers, was first discovered in the wild back in 2016. It is commonly distributed via malspam, or malicious spam, which is a type of spam email that contains malware or links to malware-infected websites. In this report, we will discuss a recent Formbook (version 4.1) infection that occurred via malspam.
How This Formbook Infection Works
In this instance it was delivered through malspam that contained a malicious Microsoft executable within a rar archive named scan copy-001.rar. The malicious Formbook dropper executable (scan copy-001.exe). The email is attempting to social engineer the victim into opening the rar attachment to execute the Formbook malware. The email contained urgent language, asking the victim to confirm that the attachment is a revised proforma invoice (which is an obvious ruse).
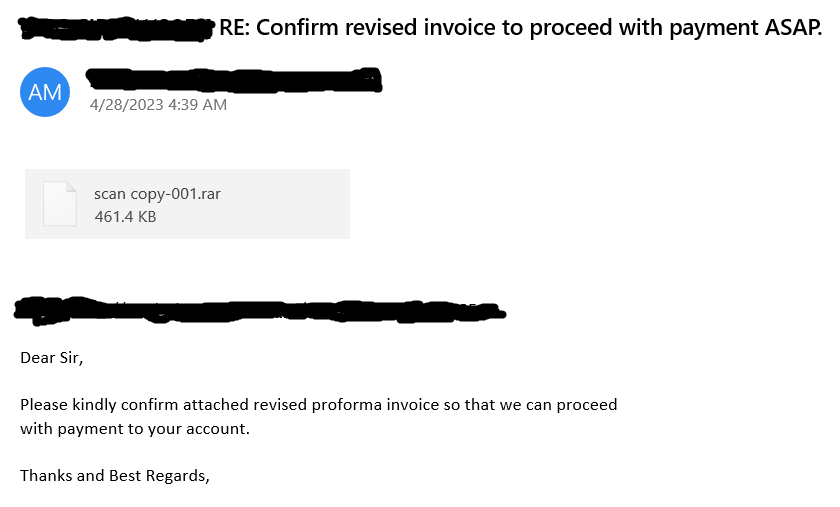
Figure 1: Formbook malspam containing a malicious rar attachment (scan copy-001.exe)
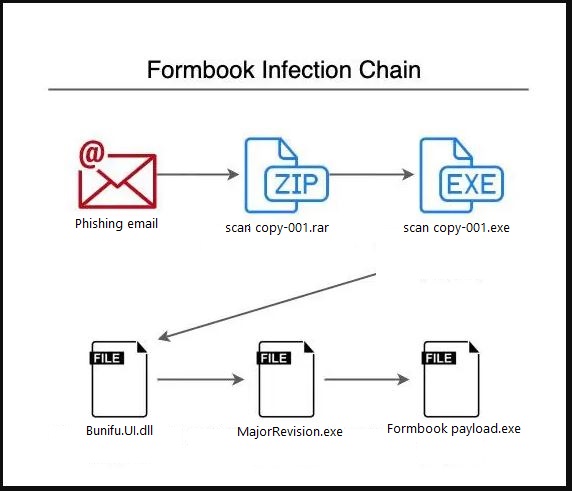
Diagram 1: This Formbooks campaign’s infection chain.
 Diagram 2: Formbook is a MAAS (Malware as a service). It is sold on underground forums.
Diagram 2: Formbook is a MAAS (Malware as a service). It is sold on underground forums.
Technical Analysis
We start our analysis with scan copy-001.exe (Formbook dropper). It is a 32-bit, .NET executable file. Upon execution of scan copy-001.exe, persistence is set by creating a scheduled task to run every time the infected user logs on:
Scheduled Task: %WINDIR%system32tasksupdatespwwigddan
C:Users<Username>AppDataRoamingpWWigddan.exe (Classification: Formbook Dropper; renamed duplicate of scan copy-001.exe)
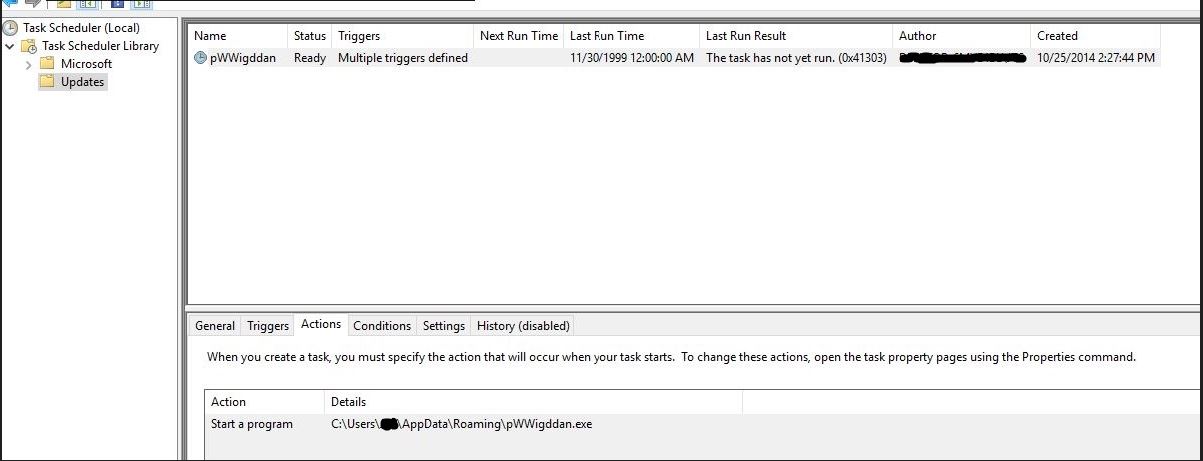 Figure 2: Creates a Scheduled Task to set persistence.
Figure 2: Creates a Scheduled Task to set persistence.
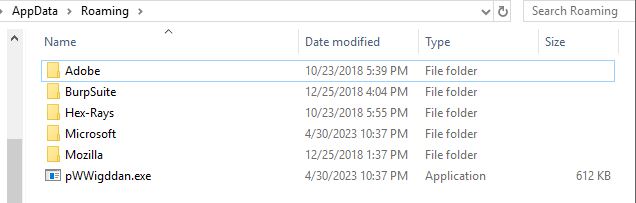
Figure 3: Drops a executable file that corresponds with the scheduled task.
The Anti-Analysis functionality includes multiple subfunctions to check for the following anti-analysis tools such as (Fig. 4 & 5):
- DebuggerHidden: explicitly tells the debugger not to step inside of the method and no break point will be hit over that method.
- EditorBrowsable: prevents the debugger from displaying code.
- DebuggerBrowsableState.Never: hides the element from the debugger.
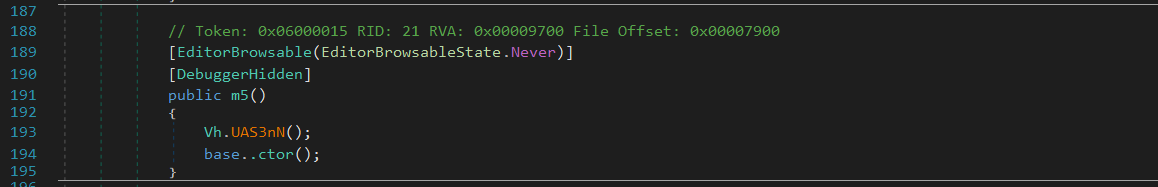 Figure 4: EditorBrowserable and DebuggerHidden functions.
Figure 4: EditorBrowserable and DebuggerHidden functions.
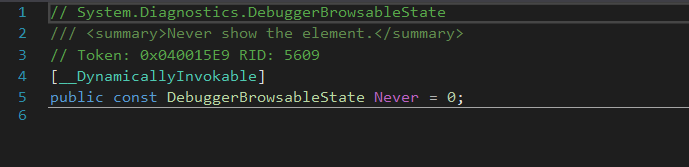
Figure 5: DebuggerBrowserableState.Never function.
The Main function decodes the hardcoded base64 encoded module named Bunifu.UI.dll and loads it in the memory using the Invoke method (Figure 6).
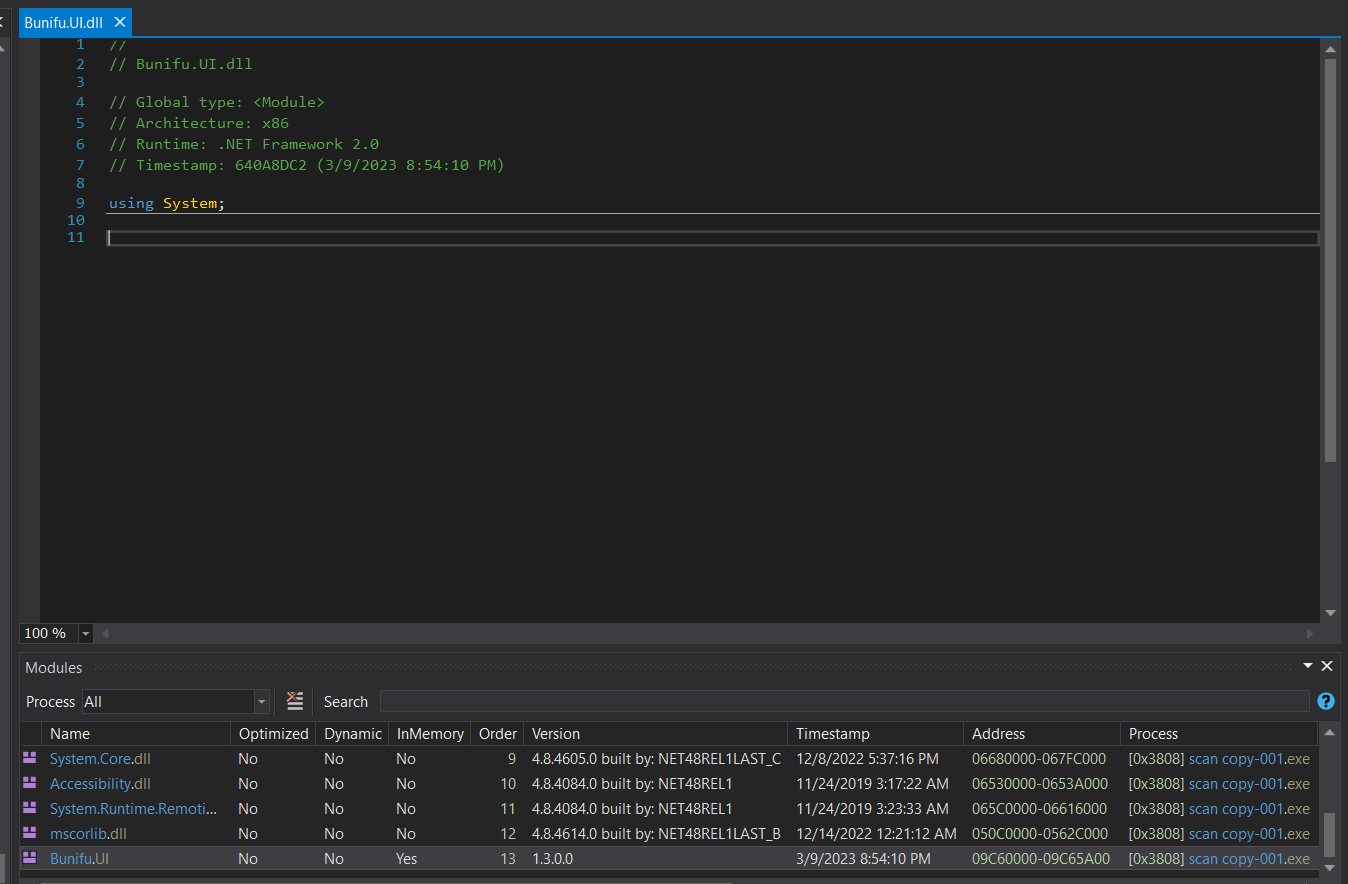
Figure 6: Scan copy-001.exe loading Bunifu.UI.dll
The new module Bunifu.UI.dll is an obfuscated .NET file that further executes a function to retrieve the embedded bitmap image named otQGDK, which is present in the resource of the malware file scan copy-001.exe.
This steganography technique is used to hide malicious content in the compressed bitmap image. The successful decompression of the bitmap image retrieves another .NET file in memory which is MajorRevision.exe (Figure 8). The Bunifu.UI.dll module then loads MajorRevision.exe using the Assembly.Load method; which passes the decompressed bitmap content as an argument and then invokes it.
Figure 7: Encrypted bitmap image (otQGDK) hiding an embedded executable (MajorRevsion.exe).
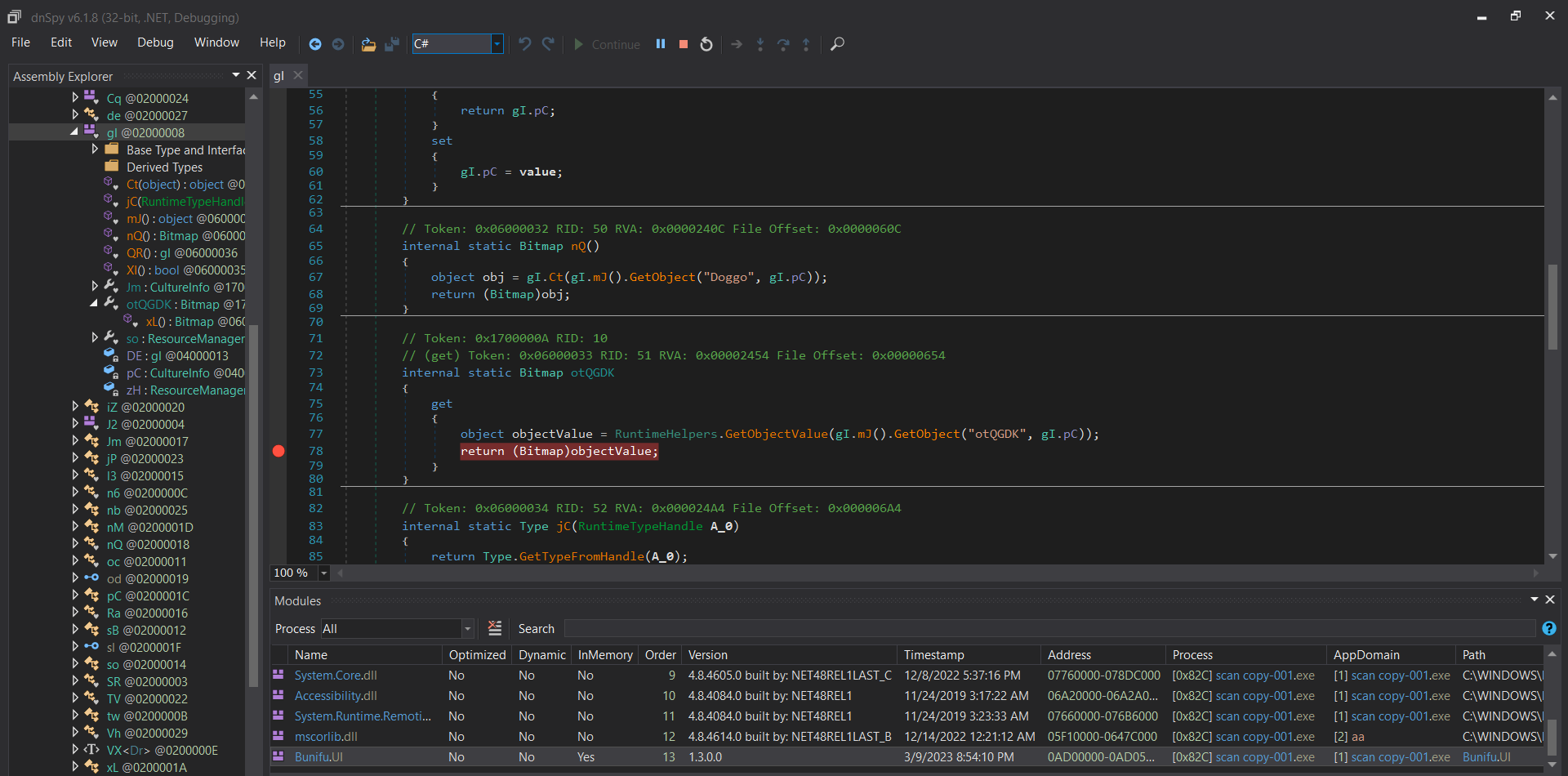
Figure 8: Successful decompression of the bitmap image retrieves another .NET file in memory which is MajorRevision.exe.
C2 Configuration Settings
Below are the decrypted hardcoded configuration settings:
{“C2 list”: [“www.despachocontablequinsa.com/m82/”], “decoy”: [“jamesdevereux.com”, “artificialturfminneapolis.com”, “hongmeiyan.com”, “lojaderoupasbr.com”, “yit.africa”, “austinrelocationexpert.com”, “saiva.page”, “exitsategy.com”, “chochonux.com”, “klosterbraeu-unterliezheim.com”, “byseymanur.com”, “sblwarwickshire.co.uk”, “brazimaid.com”, “ciogame.com”, “bronzesailing.com”, “dwkapl.xyz”, “022dyd.com”, “compassandpathwriting.com”, “alphabet1x.com”, “selfcleaninghairbrush.co.uk”, “power-bank.co.uk”, “kickskaart.com”, “baumanbilliardsnv.com”, “bestcp.net”, “doghospitalnearme.com”, “mixano.africa”, “helarybaber.online”, “illubio.com”, “ciutas.com”, “ldpr33.ru”, “killtheblacks.com”, “cassino-portugal.com”, “danhaii.com”, “gvtowingservice.com”, “let-travel.africa”, “dental-implants-67128.com”, “facetaxi.xyz”, “ctjh9u8e.vip”, “kyosaiohruri.com”, “executivepresencetrainer.com”, “greatharmony.africa”, “feelingsarereal.com”, “devopsuday.club”, “happiestminds-udemy.com”, “fittingstands.com”, “happyhousegarment.com”, “24daysofheaven.com”, “herhustlenation.com”, “xn--oy2b27nt6b.net”, “hothotcogixem.online”, “hausmeisterservice-berlin.net”, “hjddbb.com”, “stoutfamilychiro.com”, “bookishthoughtsbychristy.com”, “gibellinaheartquake.com”, “8cf1utrb6.xyz”, “patrick-daggitt.com”, “ebcbank.net”, “angel909reviews.com”, “arcteryxsouthafricaonline.com”, “cutematvhy.com”, “art2z.com”, “bulkforeverstamps.com”, “heatbling.com”]}
As with previous versions of Formbook, MajorRevision.exe communicates with multiple domains established as decoys, but it only uses one true C&C.
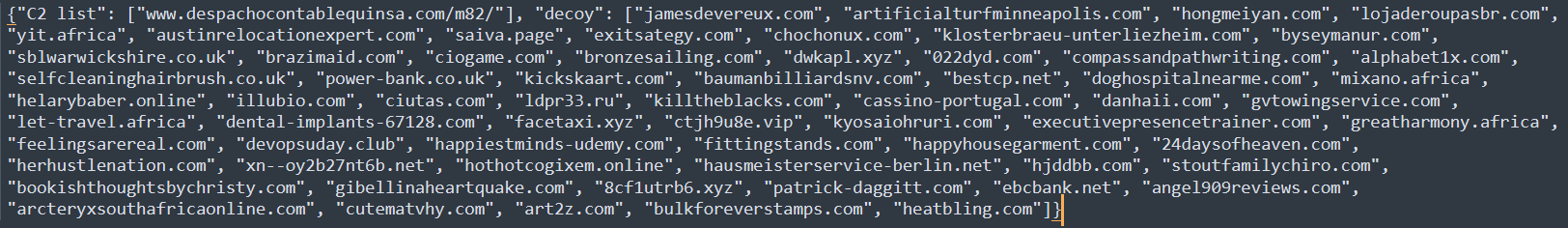
Figure 9: The C2 configuration file.
The final payload is retrieved from memory by converting a large array of bytes, this payload is then injected into a newly created process using Process Hollowing.
The final payload is categorized as Formbook, it is not a .NET application but a MASM-compiled PE32 executable that contains a single .text section.
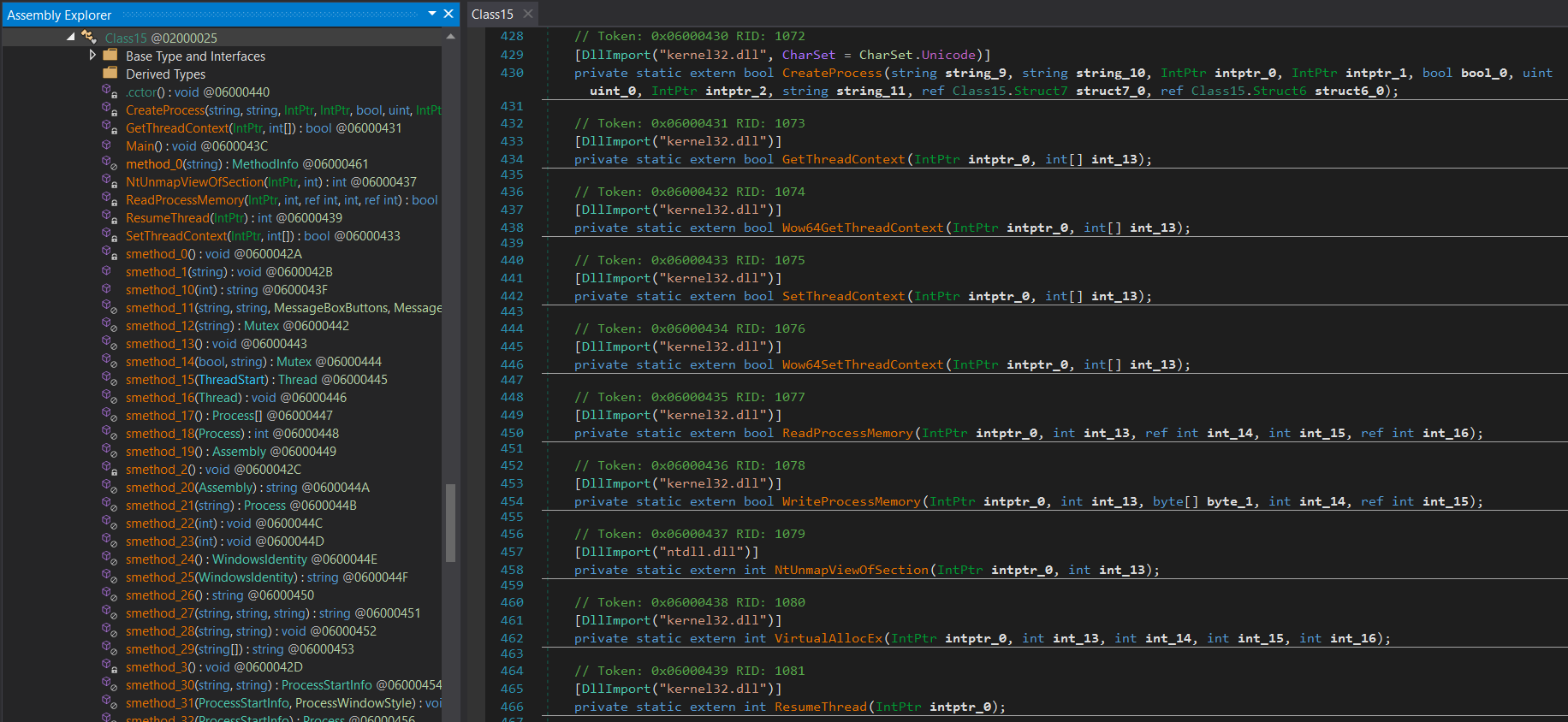
Figure 10: Functions (CreateProcess, NtUnmapViewOfSection, VirtualAllocEx, WriteProcessMemory, SetThreadContext, ResumeThread) referenced in Class15 are utilized for process hollowing.
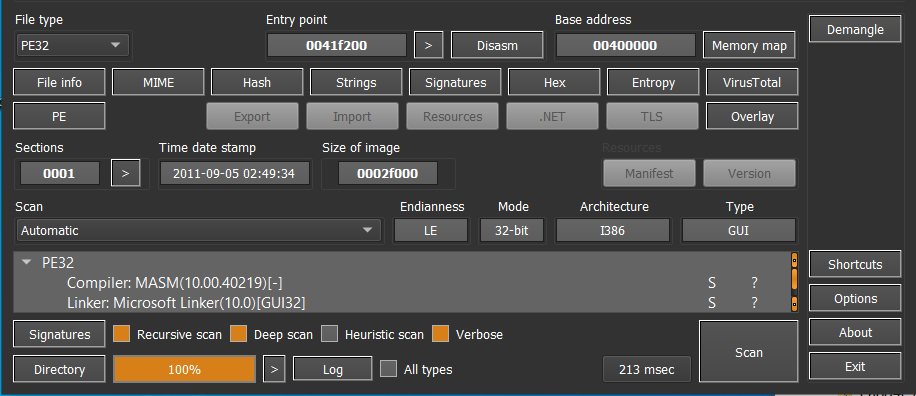
Figure 11: The final payload (Formbook) is compiled in MASM.
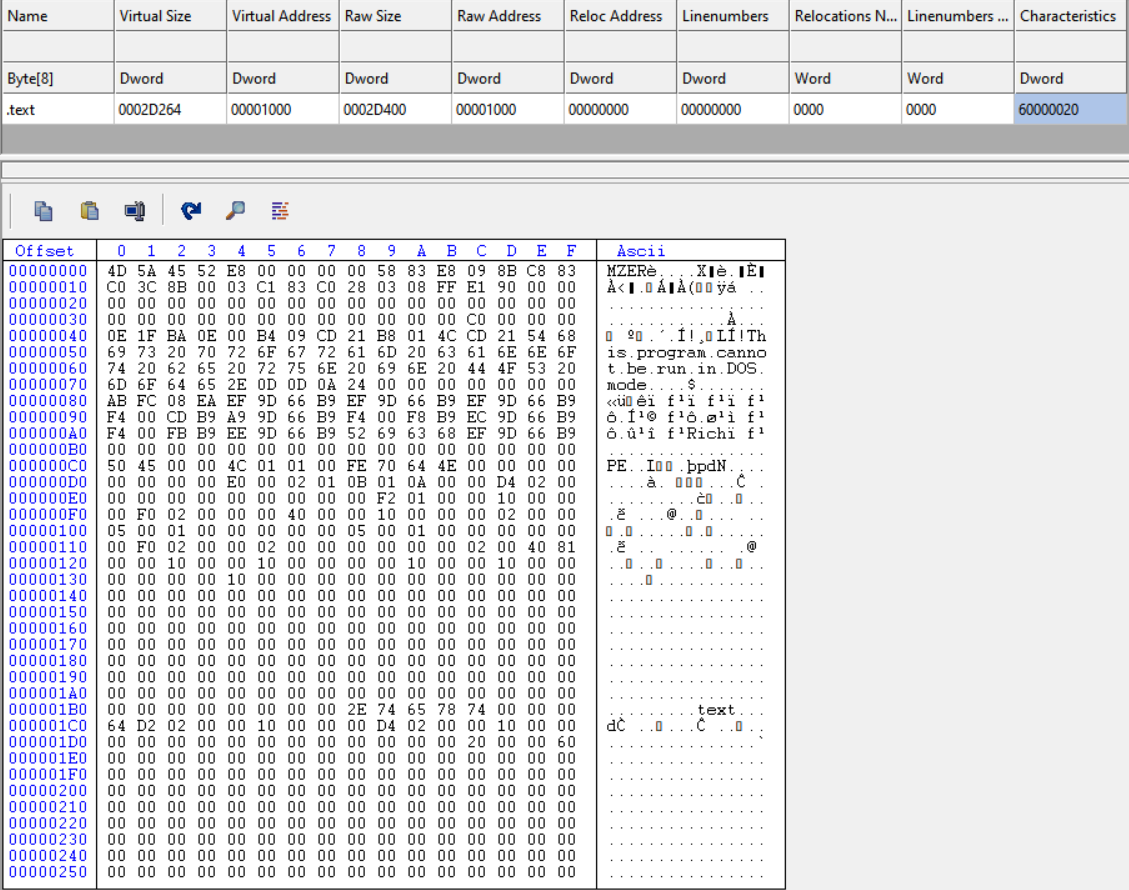 Figure 12: The final payload (Formbook) contains of a single .text section.
Figure 12: The final payload (Formbook) contains of a single .text section.
To avoid similar attacks in the future, organizations must adopt strong email security practices that include spam filters, enabling email authentication protocols, as well as user security awareness training.
Users need security awareness training to be able to recognize signs of malspam, including suspicious attachments, urgent language, and unexpected emails from unknown senders.
Additionally, organizations should utilize endpoint protection and regularly update their systems to help mitigate the risk of malware infections.
In conclusion, Formbook infections via malspam pose a serious threat to organizations and individuals.
Attackers use social engineering to trick victims into downloading malware, which could possibly result in significant data breaches and financial losses.
Organizations must remain alert and vigilant. Which hopefully will lead to the implementation of more robust security measures to help protect against these types of attacks.
IOCs:
Scan copy-001.exe – MD5: 97ab2171b12f2e2b41f65c02f23da953
Bunifu.UI.dll – MD5: 27F5124BF8F451BCA8D8A15C73C4F521
MajorRevision.exe – MD5: 93b2754b3afa34b828cb071f036a8d31
Formbook_payload.exe (Final payload) – MD5: E46809BB82201038371C602FA8B68531
