Victim Organization Themed Phishing
A victim organization themed phishing campaign is when the spammers target a specific organization by crafting and designing the phishing email and/or phishing landing page with the victim organization’s logos and designs.
How This Phishing Campaign Works
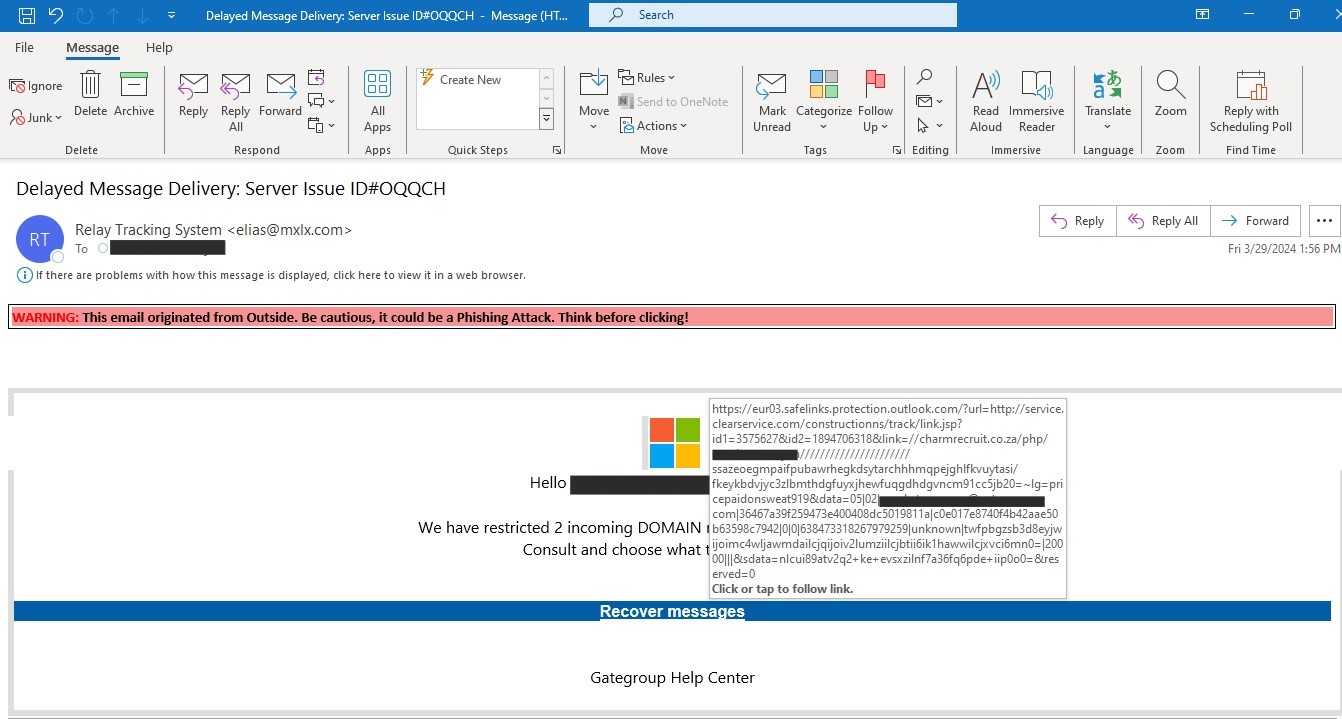
This particular phishing email campaign’s email body was Microsoft Office themed. The embedded phishing hyperlink was: hxxp://service[.]clearservice[.]com/constructionns/track/link[.]jsp?id1=3575627&id2=1894706318&link=//charmrecruit[.]co[.]za/php/[username]//////////////////////ssazeoegmpaifpubawrhegkdsytarchhhmqpejghlfkvuytasi/fkeykbdvjyc3ZlbmthdGFuYXJheWFuQGdhdGVncm91cC5jb20=~lg=pricepaidonsweat919.
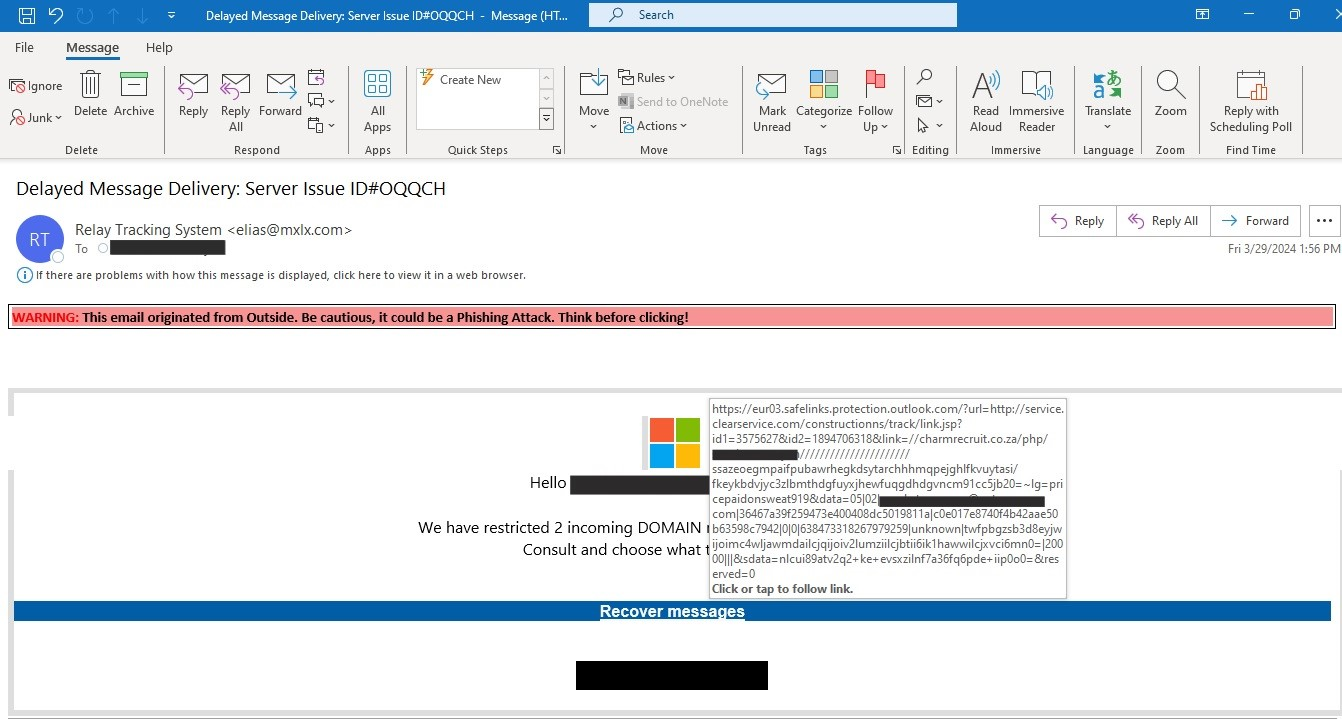 Figure 1: Microsoft Office themed phishing email with an embedded phishing hyperlink.
Figure 1: Microsoft Office themed phishing email with an embedded phishing hyperlink.
It appears that this page has JSP session tracking enabled (i.e. track/link[.]jsp?id1=[7 digit number]&id2=[10 digit number]), this page automatically redirects to:
hxxps[:]//charmrecruit[.]co[.]za/php/[username]//////////////////////ssazeoegmpaifpubawrhegkdsytarchhhmqpejghlfkvuytasi/fkeykbdvjyc3ZlbmthdGFuYXJheWFuQGdhdGVncm91cC5jb20=~lg=pricepaidonsweat919. This is a CAPTCHA page that request the victim to hold the captcha button (LABELED: Hold me) down for at least 5 seconds.
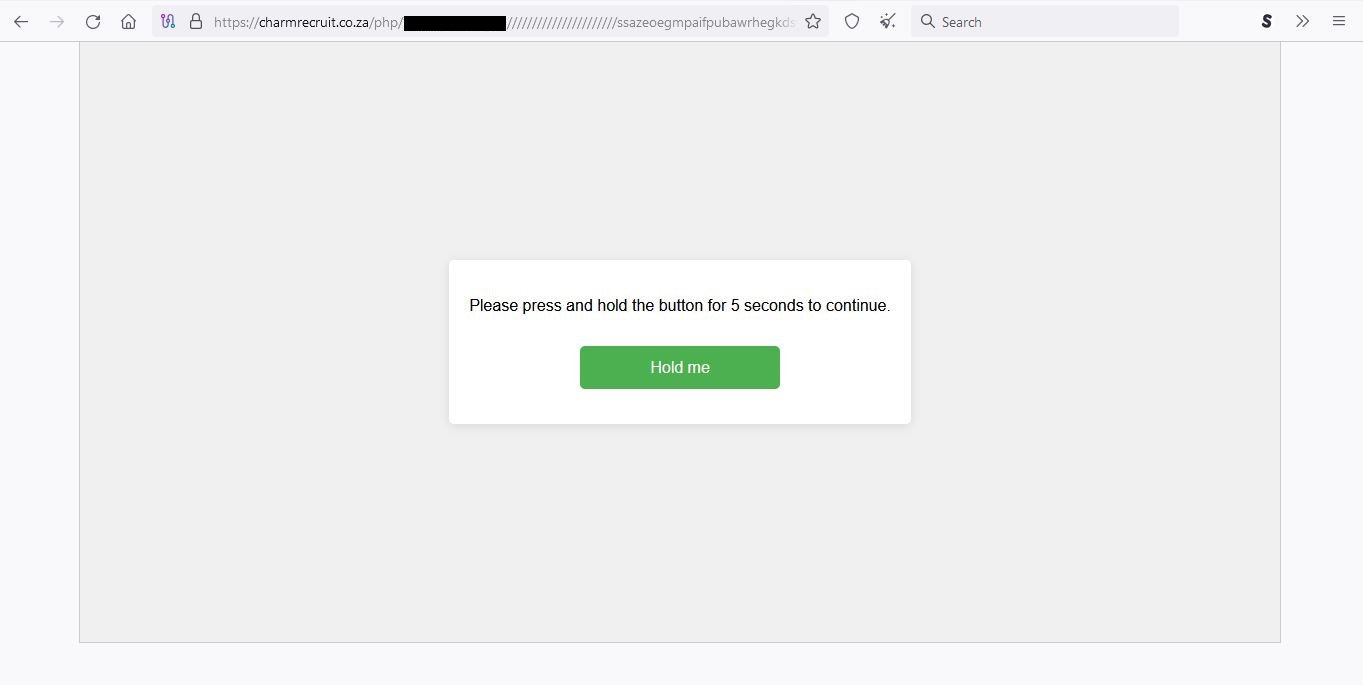 Figure 2: CAPTCHA page that request the victim to hold the captcha button (LABELED: Hold me) down for at least 5 seconds.
Figure 2: CAPTCHA page that request the victim to hold the captcha button (LABELED: Hold me) down for at least 5 seconds.
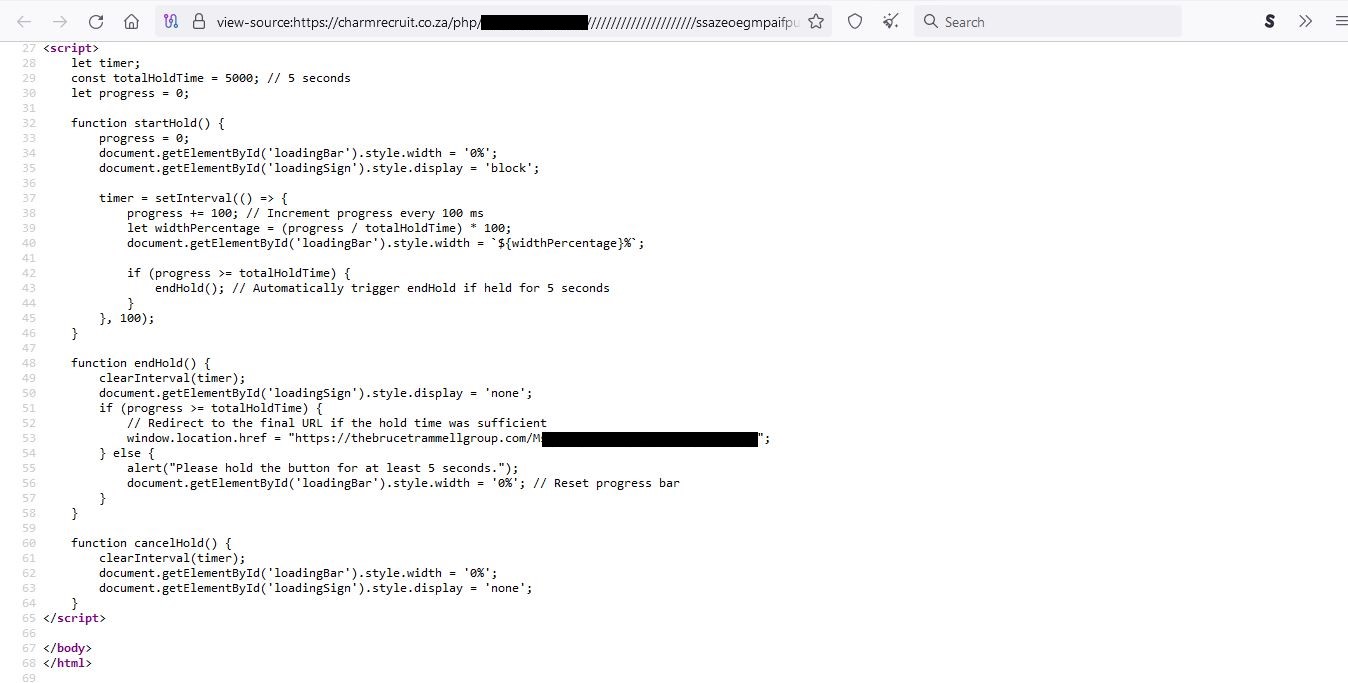 Figure 3: The CAPTCHA page’s source code, notice the startHold function that gives functionality to the captcha Hold me button.
Figure 3: The CAPTCHA page’s source code, notice the startHold function that gives functionality to the captcha Hold me button.
Then it redirects to the final phishing page:
hxxps[:]//thebrucetrammellgroup[.]com/M[victim’s email address]
This final phishing page was victim organization themed (including organization logos & designs). The user login credentials that are entered into this phishing page are posted to the domain: thebrucetrammellgroup[.]com.
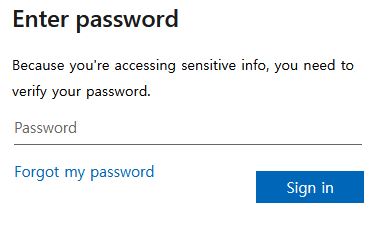
Figure 4: Final phishing page (victim organization’s themed) harvest the victim’s login credentials. The victim organization and victim email address has been cropped out.
That ends of this blog, which showed the analysis of a victim organization themed phishing campaign used to trick the organization’s employee(victim) into entering their login credentials.
Network IOCs:
hxxp://service[.]clearservice[.]com
hxxps://charmrecruit[.]co[.]za
hxxps://thebrucetrammellgroup[.]com